The Fort Knox Blockchain
From decentralised by Saurabh Deshpande
TLDR;
- Proactive Security is Essential: Digital threats are growing, and proactive security is no longer optional. It is crucial for building trust in blockchain and DeFi systems.
- Zircuit's Opinionated and Differentiated Approach: Zircuit leverages AI-Sequencer Level Security (SLS) to detect and quarantine harmful transactions before they impact the blockchain.
- Minimal Latency: Zircuit's security measures add minimal latency, with most transactions verified in just 100 milliseconds, making the process virtually seamless for users.
- Built-in Security Without Cost: Zircuit acts as zero-cost additional insurance coverage at the infrastructure level for developers. It offers enhanced security without adding expenses, encouraging safer DeFi usage and developer trust.
- Rapidly growing Ecosystem: ~$2 billion in TVL, over 50 ecosystem projects, including Catizen, the top Telegram game, and a to-be-announced exciting fair launch consumer AI app being incubated on the chain.
Hello,
Imagine if our bodies had no immune system and doctors could only treat diseases after we got sick. No antibodies to recognise and fight off threats. No fever to stop infections in their tracks. We'd be constantly vulnerable, only able to react after an illness had already taken hold. Every new virus would be a potential catastrophe.
Our industry faces a similar crisis of confidence today. Each new hack splashed across headlines is another infection, another reason for potential users to keep their money in traditional banks. Like a body without immunity, the crypto industry's future depends on its ability to detect and neutralise threats before they can cause damage.
But what if we could give blockchain an immune system? What if we could identify and quarantine malicious attacks before they spread instead of scrambling to patch vulnerabilities after millions are lost? This is where Zircuit comes in, reimagining blockchain security from the ground up.
In this article, we'll trace the evolution of financial security from physical bank vaults to digital fortresses, examine how the threat landscape has transformed, and explore how Zircuit's approach to blockchain security could finally give users the confidence they need to embrace cryptocurrency's potential.
Let's start at the beginning.
From Iron Vaults to Internet Walls
A grand building with marble floors, imposing iron vaults, and a team of watchful guards standing by. Security was a matter of physical barriers in the early days of banking. Thick steel doors and alarm systems were the height of security technology. The primary threats were tangible—robbers with guns, not hackers with keyboards. If someone wanted to rob a bank, they had to be there in person, face-to-face with the vault and the guards.
The bank's safety depended on how well they could protect their physical assets from being breached; how many guards they could post at the entrance, and the thickness of the vault that held their customers' wealth.
During this time, physical proximity was a security mechanism. To pose a threat to a bank, you had to be physically present in the same place at the same time. This limitation acted as a natural barrier, making bank robberies rare and often dangerous for the attacker. The idea that a bank could be robbed by people who are tens or thousands of miles away from the bank was unimaginable.
As banks were forced to go digital, these barriers began to crumble. Computers and the internet made geographic locations redundant when it came to bank robberies. The internet broke the traditional concept of proximity-based threats. Suddenly, a bank in the US could be attacked by North Korea by a distributed group of people—coordinated, anonymous, and invisible. A hacker sitting in their bedroom halfway across the globe could now breach a bank's defences as easily as a thief once broke through a vault door.

The first major cyber heist occurred between 1994 and 1995 when a Russian computer engineer managed to steal $10 million from Citibank using a dial-up wire transfer exploit. Since then, banks have increasingly fallen victim to sophisticated cyberattacks. One notable example is the attack on the Federal Reserve Bank of New York, where hackers compromised the account of Bangladesh's central bank and managed to successfully transfer $101 million. Fortunately, the Federal Reserve Bank of New York blocked 30 remaining transactions worth $850 million due to suspicions raised by a simple misspelling in the transaction instructions.
Beginning in 2013, another significant threat came from a group of hackers known as Carbanak. This group reportedly stole nearly $1 billion from over 100 banks across 30 countries by infiltrating their systems and mimicking legitimate transactions. Carbanak's methods were particularly alarming because they demonstrated how cybercriminals could remain inside a bank's network for months, learning its processes and executing attacks that appeared entirely legitimate.
According to the FBI’s Internet Crime Report 2023 , in the five years between 2019-23, the world has lost over $37 billion to cybercrimes.
This shift fundamentally changed the nature of security for financial institutions. Banks and fintech companies were no longer dealing with threats that could be countered with guards and alarms. They had to develop new strategies to combat invisible enemies whose attacks could come from anywhere, at any time. And thus began the race to stay one step ahead in an increasingly digital and distributed threat landscape.
Fintech Dealing with Security
In the early days of companies like PayPal and eBay, security was largely reactive, dealing with incidents after they occurred. But, as cyber threats became more sophisticated, both companies began to invest in real-time risk monitoring systems.
PayPal introduced fraud detection mechanisms that used machine learning models to analyse vast amounts of real-time transaction data. By monitoring transaction history, behavioural patterns, and geographic data, PayPal could identify anomalies that might indicate fraudulent activity. Their system used risk-scoring models to flag high-risk transactions and route them for further review. This proactive approach significantly reduced the incidence of financial fraud.
This capability became the foundation for broader applications when Peter Thiel, one of PayPal's co-founders, went on to co-found Palantir Technologies in 2003. Palantir expanded upon PayPal's pattern recognition and anomaly detection techniques, adapting them to ingest and synthesise data from various sources beyond just financial transactions.
Palantir’s tools became invaluable to intelligence agencies like the National Security Agency (NSA) and the Central Intelligence Agency (CIA). They used them to analyse vast financial records, telecommunications, and travel data. These tools were instrumental in tracking Osama bin Laden, as they could identify hidden connections, map networks, and visualise patterns that might otherwise have been missed. The same pattern and network analysis that helped PayPal fight fraud was ultimately used to map out bin Laden's courier network and trace money flows, leading to his location in Abbottabad, Pakistan.
E-commerce giant eBay followed a similar path by implementing thorough buyer and seller protection programs. They used data analytics to monitor activity patterns and spot irregular behaviours, such as rapid changes in pricing or repeated attempts to sell high-risk items. Additionally, eBay developed reputation systems for buyers and sellers, which helped in identifying potentially fraudulent accounts early. By combining machine learning models with data-backed insights, eBay was able to flag and investigate suspicious activities before they escalated. This resulted in improved platform security.
Similar advancements took place in the banking industry as well. For instance, when I use my credit card from India’s HDFC Bank while travelling in Dubai, I receive a call from the bank to verify my identity. This typically occurs for transactions that exceed my usual spending patterns. Receiving these calls for every small purchase, like buying coffee or dinner, would be both irritating and inefficient. So, implementing spending analysis to identify unusual transactions in real-time makes sense.
These efforts exemplify how the evolution of security measures in the Web2 world has focused on proactive threat detection and response instead of waiting for something to happen and then reacting to it. Ultimately, it improved user trust and safety.
But it is not hunky dory in the Web2 world either. McKinesy’s 2019 research on financial crime and fraud highlights how banks often underestimate the total cost of financial crime, fraud, and cybersecurity. Beyond direct fraud losses, there are significant indirect costs such as regulatory fines, customer attrition, transaction declines, and system unavailability. Including these costs provides a more comprehensive understanding of the impact of financial crimes on institutions.
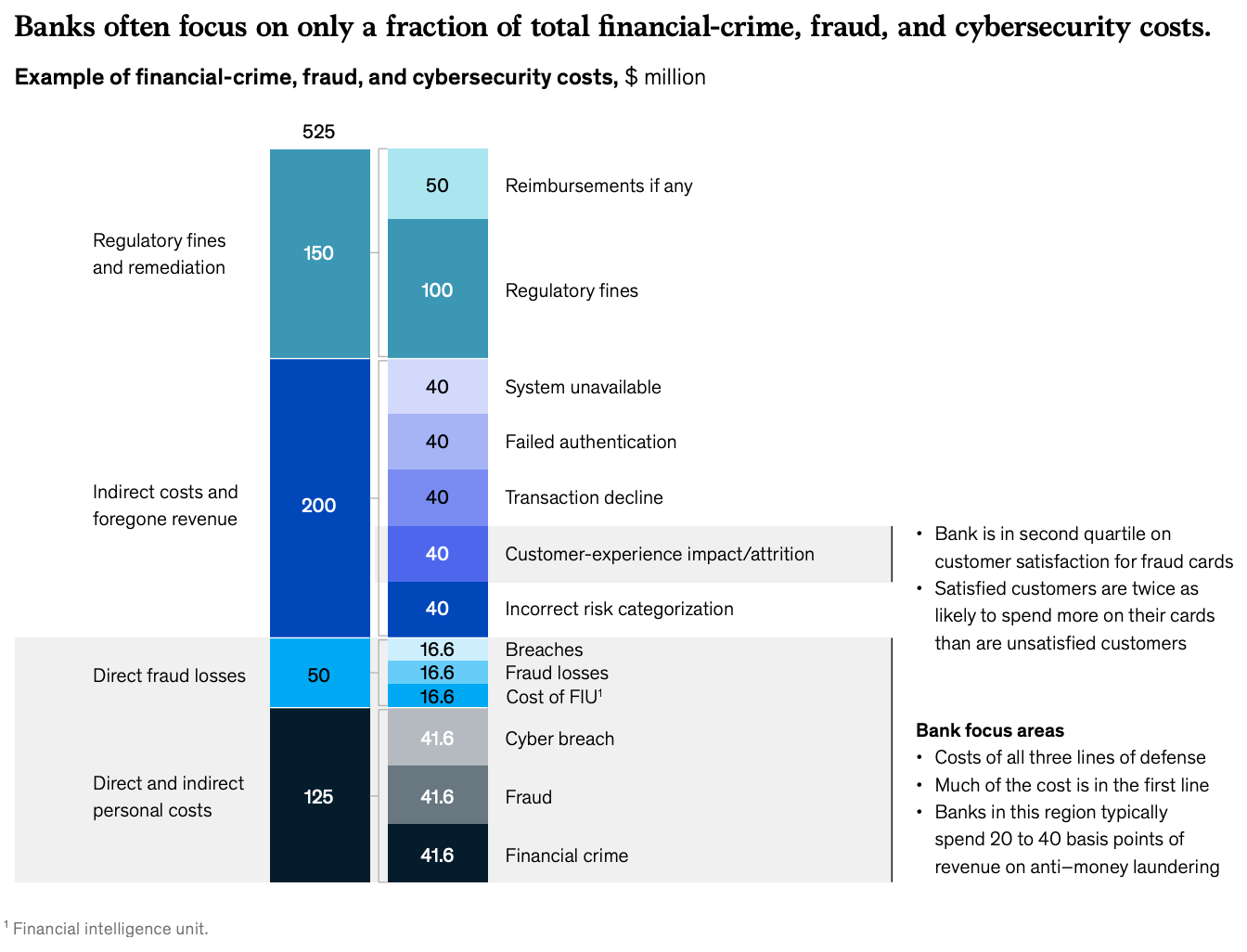
Source: Mckinsey
By focusing only on direct losses, many institutions fail to address the broader implications that can deeply affect their reputation and customer experience. This leads to an important question: how can these indirect impacts be mitigated effectively? Could there be a more proactive, real-time approach to prevent issues before they escalate?
Security in Crypto
According to Slow Mist, crypto has lost to the tune of $33 billion in different hacks since 2012. Out of close to 1700 incidents, the chart shows the top few categories of attacks. Contract vulnerability and rug pulls are the leading causes of lost funds.
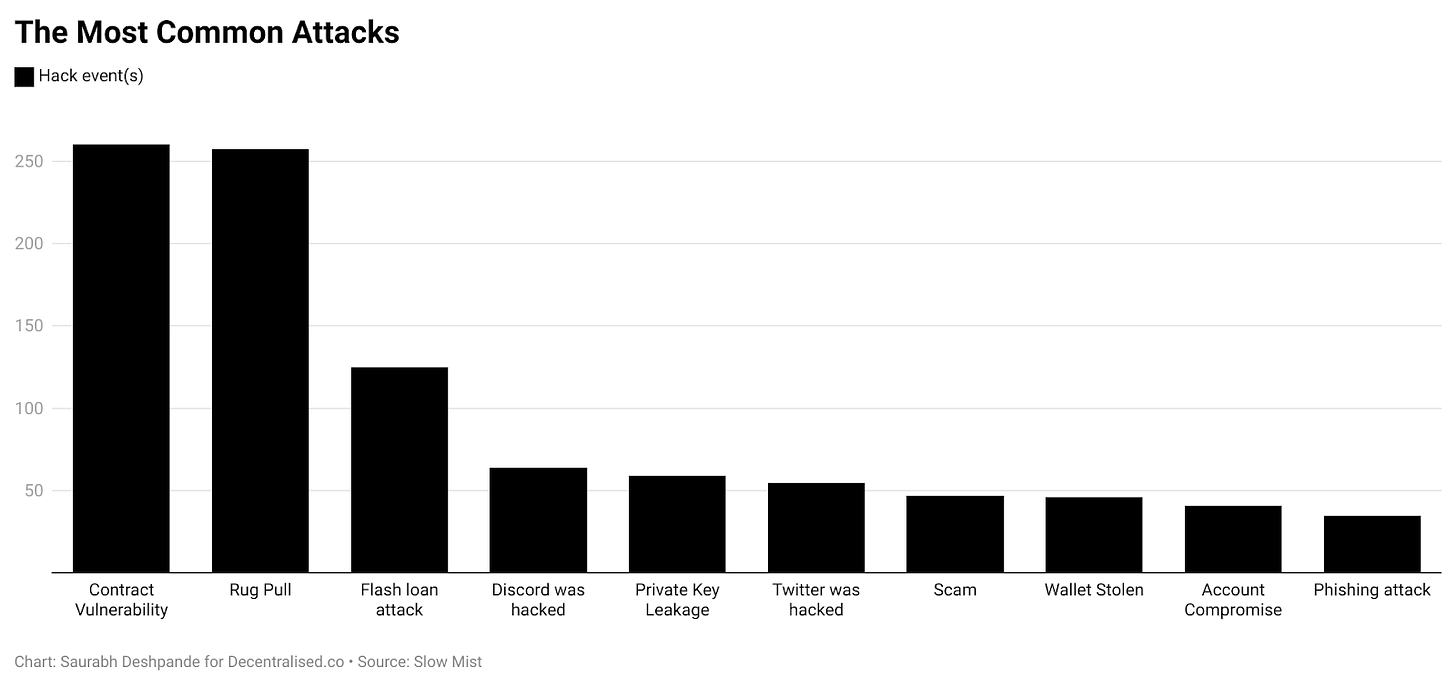
Chainalysis report s the amount received by illicit addresses is far higher. 2023 alone sees $24 billion transferred to illicit addresses. The difference in the amounts could be because of how Chainalysis accounts for illicit addresses, whereas Slow Mist focuses on specific blockchain incidents. Crypto’s ongoing battle with hacks and security breaches is like a persistent cold that just won't go away. These incidents don't just burn a hole in people's pockets; they make a massive dent in the industry's reputation.
Imagine you're about to try a new restaurant, but every other review mentions food poisoning—you'd probably give it a miss, right? That's what's happening with crypto. Each hack is another reason for potential users to stick with their trusty old banks.
These security nightmares also give regulators sleepless nights. Every time a major hack hits the news, it's like ringing a dinner bell for watchdogs. They swoop in with a flurry of new rules and regulations, often leaving crypto companies feeling like they're navigating a minefield blindfolded. While some oversight is necessary, this reactive approach to regulation can be heavy-handed, potentially stifling innovation.
It's a bit like using a sledgehammer to crack a nut—effective, sure, but it might just pulverise everything else in the process. This regulatory pressure and the trust issues arising from repeated hacks create a perfect storm that's keeping crypto from achieving mass adoption. Instead of focusing on cool new features or real-world applications, many crypto projects find themselves playing an endless game of whack-a-mole with security threats and compliance issues.
Our dream is that crypto operates at the scale of the internet. Perhaps that will happen five or ten years from now. But are we ready? When a few billion people use crypto daily, the potential for fraud increases manyfold. We can’t build security then. We have to work towards it now.
We need solutions to break the cycle of hacks and regulatory crackdowns. This is where Zircuit steps in with a fresh perspective. By analysing the categories of attacks mentioned earlier, Zircuit has identified patterns in how malicious actors operate. While these bad actors often seem to be one step ahead of protocols, Zircuit posits that leveraging artificial intelligence to process this data could be a game-changer. Their thesis is that by feeding information about past attacks into an AI system, it's possible to predict and prevent at least some instances of future attacks. This proactive approach not only enhances security but could also help ease regulatory concerns by demonstrating a commitment to robust, forward-thinking protective measures.
OpenSea: A Story of Proactive Security
OpenSea was the leading marketplace for non-fungible tokens (NFTs) until mid-2022. But with great popularity came great responsibility. As the platform grew, so did the challenges of keeping users safe from deception. The marketplace was awash with fake content. Many users, especially those new to NFTs, struggled to distinguish between original creations and copymints. OpenSea knew that to fulfil its mission of making NFTs open and accessible, trust and safety had to be at the forefront.
Recognising the need for change, OpenSea made several security improvements. One of them was a partnership with Scale AI to build an advanced detection system. This collaboration marked a turning point in OpenSea's journey towards creating a safer platform for all users.
OpenSea needed a solution that could handle millions of NFTs weekly, processing them with speed, accuracy, and consistency. With Scale AI's expertise, they implemented a real-time fraud detection system. The system could scan newly minted NFTs, determine if they were copymints, and flag them for removal—all within seconds. By swiftly identifying and removing fake NFTs, OpenSea significantly reduced the risk of users purchasing fraudulent items.
But OpenSea's proactive approach didn't stop there. Like a diligent librarian ensuring every book is in its rightful place, OpenSea conducted full catalogue scans to catch any fraudulent NFTs that might have slipped through initially. These scans processed hundreds of millions of NFTs, providing an additional layer of security.
Handling such massive amounts of data presented its own challenges. With up to 50 million items needing processing each week, precision was paramount. Machine learning models helped handle this volume with an impressive 95% average precision rate.
By combining real-time detection, batch scans, and sophisticated data handling, OpenSea created a safer and more trustworthy marketplace. Users could now browse, buy, and sell NFTs with greater confidence. OpenSea's story exemplifies the power of proactive security in the digital age. It demonstrates that even in a rapidly evolving landscape, building trust through innovation is not just possible—it's essential.
The need for security in the blockchain space is even more critical due to the irreversible nature of blockchain transactions. Unlike Web2 platforms, where central authorities can intervene and reverse transactions or help recover assets, blockchain transactions cannot be reversed. This makes proactive security essential. OpenSea has shown the importance of building strong security systems to prevent malicious activities. But, if we are to follow what OpenSea did, every application will have to spend significant resources on security. Can we do something at the infrastructure level so that applications don’t have to worry much about security?
Enter Zircuit. Its proactive Sequencer Level Security (SLS) aims to address these challenges head-on, not at the application level but at the infrastructure level. This means that individual applications have an additional layer of security. Extending our banking analogy, Zircuit provides applications with bars and locks. Zircuit aims to do this by detecting and quarantining harmful transactions before they can impact the blockchain. Imagine it as an extra layer of security, similar to a gatekeeper that carefully checks each transaction before allowing it into the record.
To understand how Zircuit secures this process, imagine an airport where every passenger and their belongings go through multiple security checkpoints before boarding. In the same way, Zircuit adds multiple layers of verification to ensure that only safe transactions are processed. Now, let’s explore the basic building blocks of a Layer 2 (L2) system and how Zircuit has modified the OP Stack architecture to improve its functionality.
The Basic Building Blocks of a Layer 2 System
Imagine the blockchain as a rapidly expanding metropolis. As more residents (users) flock to this digital city, the streets (Layer 1) become congested, slowing down every transaction. Layer 2 (L2) solutions are like constructing a network of elevated highways and underground tunnels, allowing for faster travel without disrupting ground-level traffic. Let's explore the key components of these blockchain superhighways in greater detail.
Execution: The City's Brain CentreAt the heart of any L2 solution is the execution component, which acts like the city's brain centre. It processes transactions, manages the overall state, executes smart contracts, and handles deposits. Picture it as a command hub that controls all the key functions of the city, directing every operation smoothly. It ensures that power, water, transportation, and communication systems all work in harmony.
Just like a brain ensures that every part of the body performs optimally, the execution layer guarantees that all transactions are processed efficiently, account balances are updated accurately, smart contracts are executed properly, and deposits from L1 are integrated seamlessly. As the blockchain grows, this brain centre ensures the system can handle increasing demands, keeping everything functioning seamlessly.
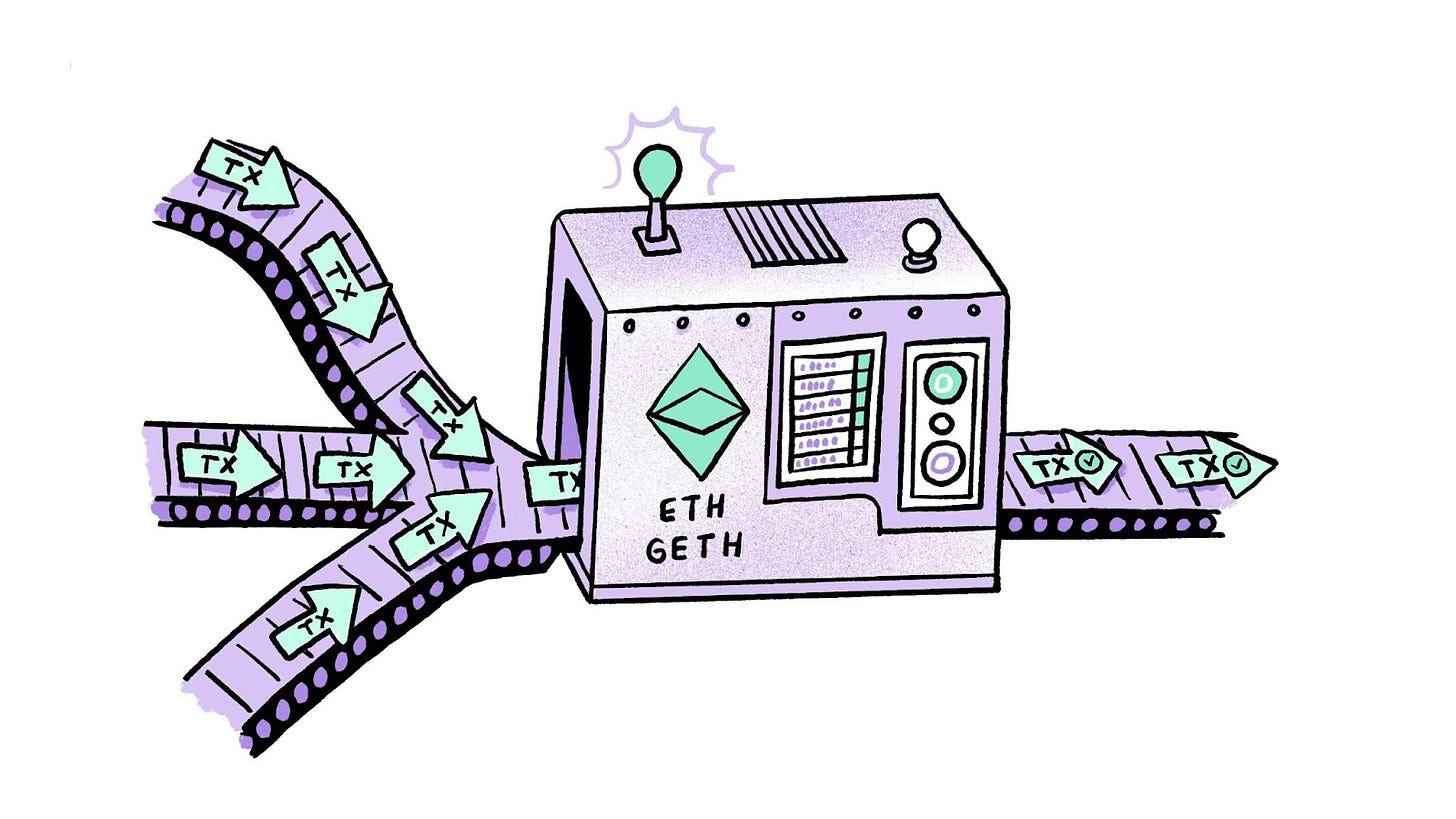
Sequencing: The Master Traffic ControllerThe sequencer in an L2 system acts as a high-tech traffic controller in a bustling control room. It doesn’t just react to congestion; it anticipates it, coordinates traffic, and opens or closes lanes to keep things flowing smoothly.
In blockchain terms, the sequencer determines the order in which transactions are processed, greatly impacting the state of the blockchain. It’s like choreographing a complex dance of data to ensure every step is perfectly timed and executed.
Currently, the sequencer in Zircuit is centralised, which allows for faster transaction processing. However, this also introduces certain challenges and responsibilities, much like having one highly efficient control centre managing an entire city's traffic. This can, however, be decentralised over time.
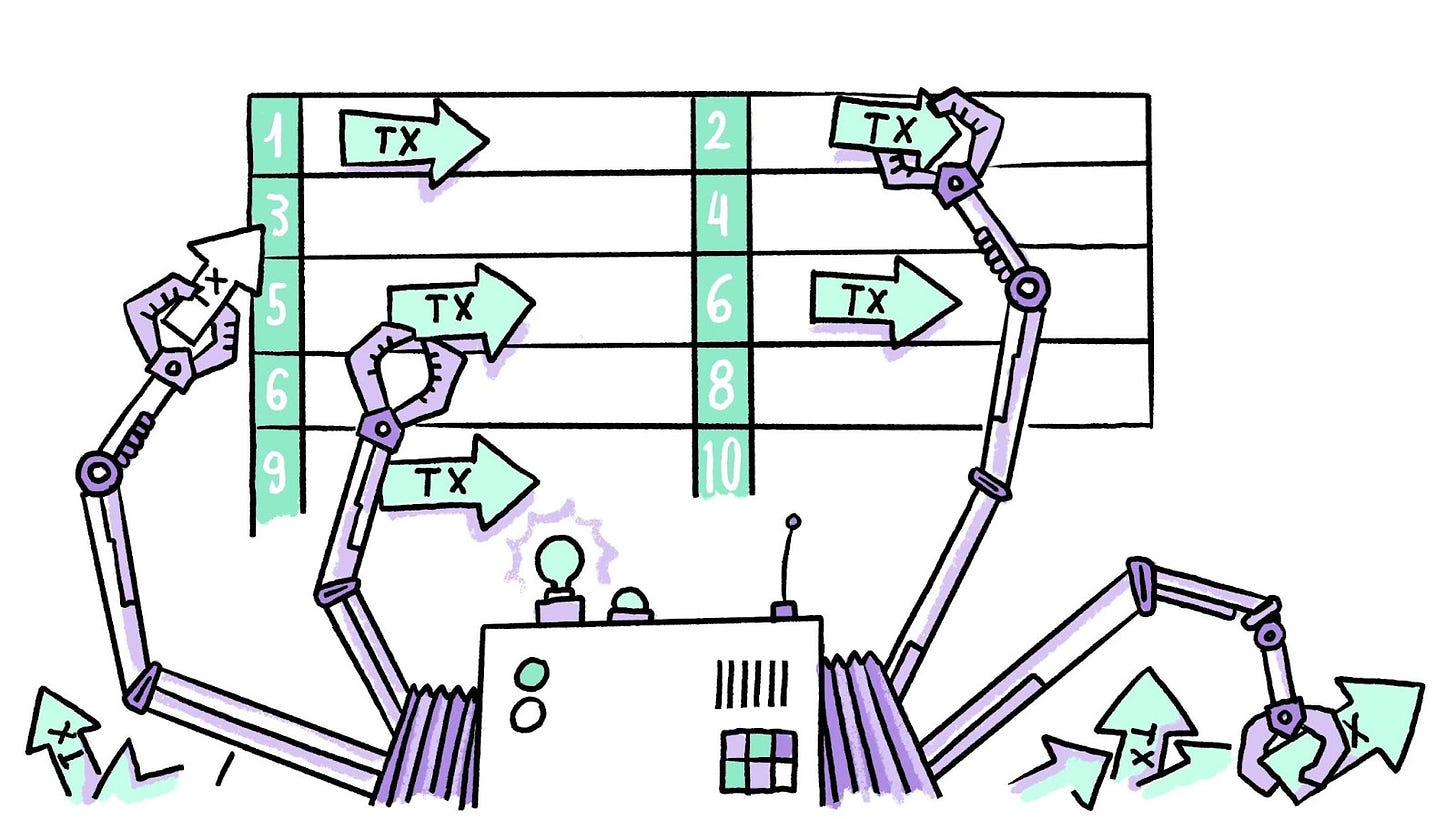
Batching: The City's Express Bus SystemBatching in L2 is like running an express bus system in our growing city. Instead of every person (transaction) taking their own car, batching groups multiple transactions together—much like passengers on a bus.
These grouped transactions are then posted to the L1 as "blobs." Picture these buses using dedicated express lanes to quickly transport groups to the city centre (L1). This significantly reduces congestion and costs, just as an efficient public transport system eases traffic and lowers travel expenses. In Zircuit, this is managed by a component called the 'batcher', which doesn’t just group transactions randomly but compresses them to reduce the gas cost of recording data to L1—much like a bus system optimising routes for fuel efficiency and convenience.
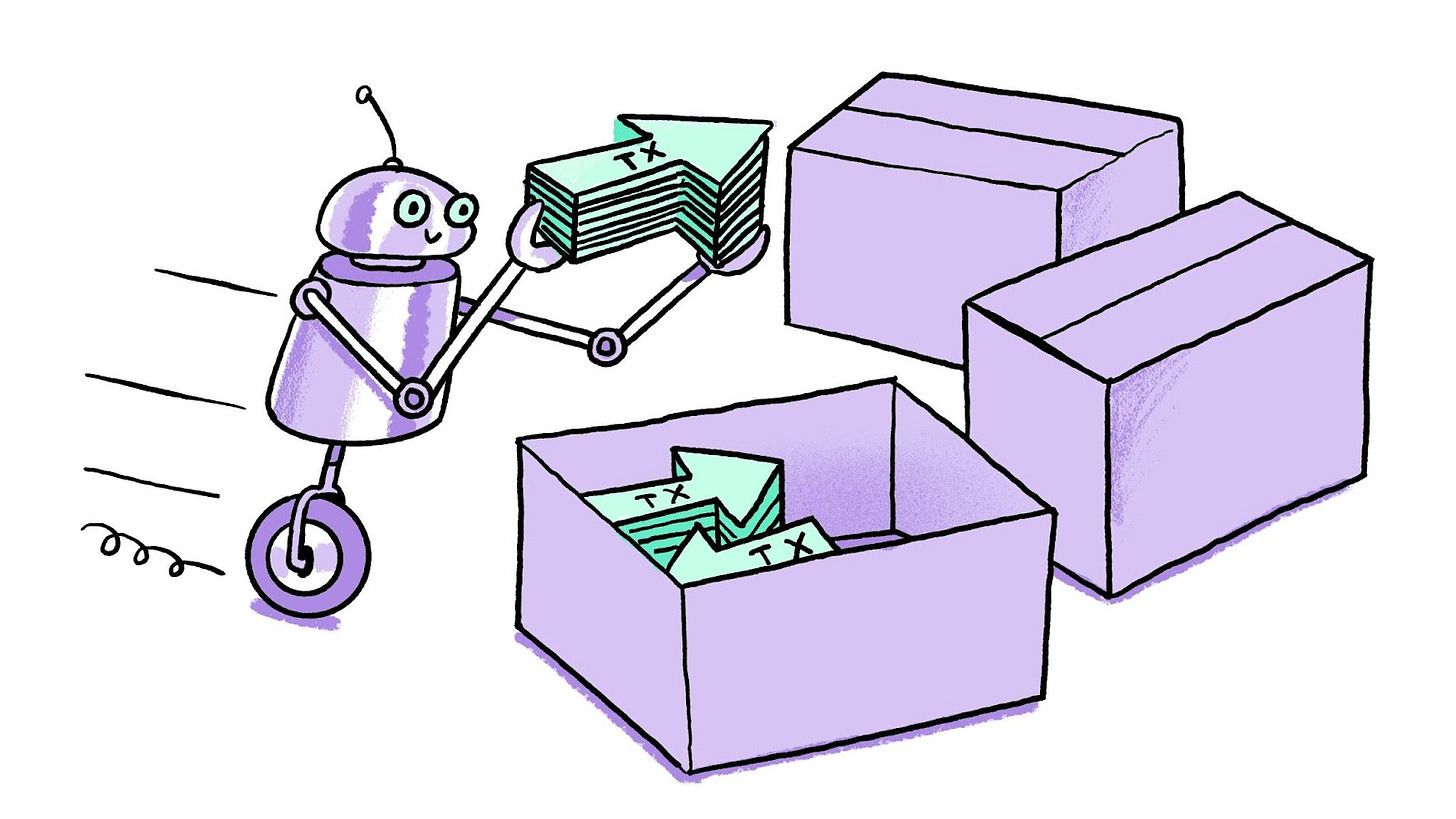
State Root Proposal: The City Planning Record KeeperThe state root in blockchain can be thought of as a city planner’s record keeper. After development and changes in the city (transactions in L2), the city planner (proposer) submits an updated master or blueprint plan to the city council (L1 blockchain).
It summarises the city's current state rather than every detail of each building or road. In blockchain terms, the proposer takes the current state of all transactions and posts this summary to L1, ensuring that the main blockchain has an accurate overview of what’s happening in L2.
The state root is critical for maintaining security and synchronisation between L1 and L2. It allows L1 to verify the validity of L2 operations without processing every single transaction—much like how a city council can approve changes without inspecting every brick laid. But be sure that even if you make changes to a single brick in the city, the city council will know that you attempted to change something. This is because when you change even one brick, the change is reflected in the new blueprint.
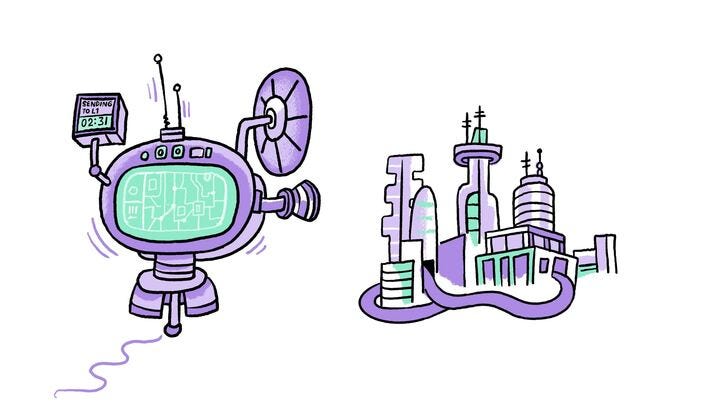
Prover: The City's InspectorThe prover is like an inspector who verifies that everything is in order. In Zircuit, ZK circuits are used by the prover to create zero-knowledge proofs, which verify that transactions are correct without revealing sensitive details. To boost efficiency, Zircuit divides the prover into smaller components for parallel processing, similar to having multiple inspectors checking different parts of a vehicle at the same time. This makes the verification process faster and more scalable, which is crucial for maintaining high transaction throughput and security.
ZK Circuits and their Role In simple terms, ZK circuits are like electronic circuits but for mathematical proofs. Just as an electronic circuit is made up of various components that work together to control the flow of electricity and produce a specific outcome, ZK circuits are made up of logical components that perform specific calculations to prove that something is true without revealing the underlying details. In the context of Zircuit, ZK circuits are used to create "zero-knowledge proofs," which verify that transactions are legitimate without needing to expose all the sensitive information involved. This makes the verification process both private and secure.
Think of ZK circuits as a series of switches in an electronic circuit. When certain conditions are met, the switches are turned on, allowing the proof to be generated. This process ensures that all the criteria for a valid transaction are satisfied without revealing the actual data behind those conditions.
Zircuit's Modifications to OP Stack
Zircuit has taken the OP stack blueprint and transformed it into a city of the future, optimising every step to enhance security and efficiency. Let's dive deeper into the key modifications that make Zircuit stand out.
Parallel Proving: The Multi-Dimensional Inspection TeamProving is one of the most resource-intensive tasks in a ZK rollup. The process of generating zero-knowledge proofs involves complex calculations that can be demanding, especially with a high transaction volume. Zircuit's solution is to split the prover into eight specialised components. This parallelisation is like having a multi-dimensional inspection team, where each inspector focuses on a different aspect of verification, such as signature checks, state transitions, or arithmetic operations.
By breaking down the proving process, Zircuit dramatically speeds up proving facts about the execution of blocks while ensuring a thorough examination of every transaction component, thereby maintaining both speed and precision.
Proof Aggregation: The Holographic City ModelAfter the parallel proving, Zircuit compiles all individual inspections into one comprehensive proof—similar to creating a holographic model of the city that incorporates all individual inspection reports. This aggregation step ensures that the final proof is comprehensive and compact, reducing both the verification time and cost on L1, which is crucial for maintaining scalability without sacrificing security.
EIP-4844 Implementation: The Teleportation GridZircuit leverages Ethereum's new data availability feature (EIP-4844) to post transactions as "blobs" on the mainnet. Imagine if our futuristic city developed a teleportation grid—goods and people are converted into data (blobs) and reassembled at their destination. EIP-4844, also known as proto-danksharding, is a significant upgrade to Ethereum that allows for more efficient data storage. By implementing this, Zircuit reduces the cost and complexity of posting data to L1. It helps enhance the system's scalability and cost-effectiveness, which benefits all users by keeping transactions affordable.
With these modifications, Zircuit has reimagined how transactions flow through a Layer 2 system to create a more efficient and secure network. To better understand how all these components work together, let’s walk through the supply chain of a Zircuit transaction—from the moment it's created to the point where it becomes a permanent part of the ledger.
The Journey of a Transaction in Zircuit
- Initial Security Screening and Sequencing: When a transaction first arrives at the sequencer, it encounters Zircuit's security oracles, which form the heart of the SLS protocol. Much like parcels going through airport security, each transaction undergoes an immediate scan for potential threats, a process completed in roughly 100 milliseconds. Should the security oracles flag anything suspicious, the transaction is promptly diverted to quarantine for a more thorough inspection. Transactions that pass this initial screening advance to sequencing, where they're organised for inclusion in the next block.
- Block Creation and Chain Extension: Approved transactions are gathered into blocks, rather like sealed containers ready for shipping. Zircuit produces new blocks every two seconds, steadily extending the L2 chain. As each block is created, it updates the local state, making transactions final at the L2 level.
- Batching for L1: Instead of posting each transaction individually on the data availability (DA) layer, Zircuit uses a component called the "batcher" to group transactions together. It is like containers on the ship. Each small container is like a transaction, and the ship is the batch. The batcher posts these grouped transactions onto the main blockchain in units called "blobs." This makes the process more efficient, allowing multiple transactions to be processed together. This results in reducing the costs and workload on the main network.
- Parallel Proof Generation: To ensure that transactions are legitimate, Zircuit breaks down the verification process into smaller steps that can be handled simultaneously. This is like having multiple inspectors check different parts of a shipment at the same time to speed things up. Zircuit has split its prover—the part responsible for proving transactions are correct—into eight smaller provers. This parallelisation makes it possible to verify transactions faster and more efficiently.
- Proposing State Roots: After the transactions are batched and proofs are generated, a "proposer" takes the state of all transactions and posts it onto the L1. You can think of this as someone summarising the contents of all the packages and officially recording that summary with a trusted authority. This summary, called the "state root," helps ensure that everyone agrees on the current state of the blockchain. If you make the slightest change, the summary will not match, and you will get caught for making the change.
- Aggregation and Submission: Once all the smaller proofs are complete, Zircuit gathers them into a single, comprehensive proof. This proof is then submitted to the main blockchain for verification. Imagine taking all the inspection reports and compiling them into one final document that gets reviewed by a trusted authority. This comprehensive proof covers multiple blocks of transactions, ensuring everything is in order before they are permanently recorded.
- Quarantine Management: If the oracle flags a transaction as suspicious during the initial verification, it's diverted to quarantine—a secure holding area where potentially harmful transactions undergo additional scrutiny. Think of it like a special inspection area where suspicious packages receive extra attention. During quarantine, transactions undergo in-depth examination using both automated checks and, where necessary, manual reviews by security experts. This process ensures that no potentially harmful transaction can impact the blockchain while legitimate transactions continue flowing through the system.
This carefully orchestrated process ensures both security and efficiency, with SLS providing protection from the earliest possible moment in a transaction's lifecycle. The system maintains its vigilance without compromising on speed, processing legitimate transactions swiftly while keeping a watchful eye for potential threats.
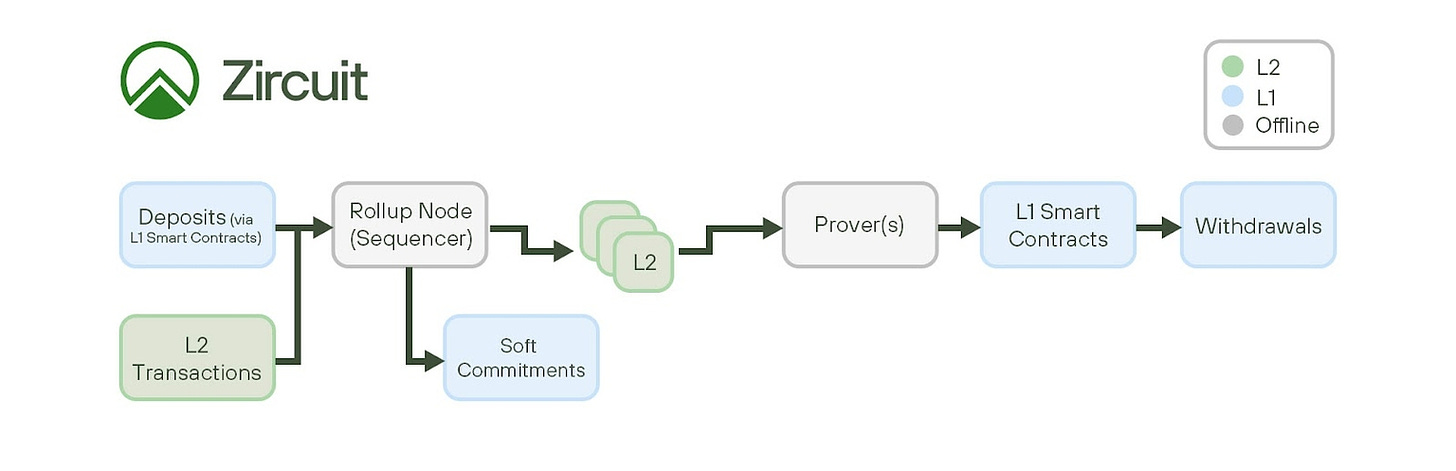
Source - Zircuit Documentation
Now, think about what it would mean if we could take all of these preventative measures one step further—creating not just a reactive but a proactive defence system. Imagine a world where crimes can be stopped before they happen. That's the premise of the sci-fi thriller " Minority Report ." Now, picture that same predictive power applied to blockchain transactions. That's essentially what Zircuit has set out to achieve with its innovative Sequencer Level Security (SLS).

While the components we've discussed so far are common to many L2 solutions, Zircuit sets itself apart with its security system. Think of SLS as the Department of Precrime of the blockchain world, identifying and neutralising potential threats before they can materialise.
Just as the precogs in "Minority Report" could foresee criminal activities, Zircuit's SLS can detect malicious transactions before they impact the blockchain. This isn't just a security upgrade; it's a paradigm shift in how we approach blockchain safety.
Let's dive into the three main components of this security system:
SLS and Its Role in Zircuit
Zircuit’s SLS is designed with three main components: Malice Detection, Quarantine-Release Criterion, and Transaction Execution. These components work together to enhance the sequencing process, ensuring that harmful transactions do not affect the blockchain state.
Malice Detection: The Precognitive Defense GridThis is a defence system capable of detecting threats before they even fully materialise. As transactions approach the Zircuit sequencer, they first encounter the Malice Detection module. This is like having a team of precogs from "Minority Report" scanning each transaction for potentially malicious intent.
This system doesn't just look at the transaction in isolation. It performs a dependency analysis, understanding how each transaction might interact with others. It's as if the precogs can see not just individual crimes, but entire networks of criminal activity before they happen.
Benign transactions, which are more than 99.9% (malicious are only a few thousand out of billions) of total transactions, are swiftly ushered through to be included in the next block. If a transaction raises red flags, it's immediately flagged for further scrutiny. This proactive approach ensures that potentially harmful interactions are identified and managed long before they can impact the blockchain.
Quarantine-Release Criterion: The Isolation ChamberTransactions flagged as suspicious are whisked away to a quarantine zone in ~100ms, faster than you can say the word "blockchain". In this holding area, suspicious transactions undergo rigorous verification processes. It's like subjecting them to a gauntlet of tests across multiple timelines and realities. The AI systems analyse every aspect of the transaction. In some complex cases, human experts can step in, like interdimensional judges passing the final verdict.
This quarantine mechanism ensures that no potentially harmful transaction sneaks through to the blockchain. Only when a transaction meets specific release criteria, proving its benign nature across all possible scenarios, is it allowed to proceed.
Transaction Execution: The Reality Integration ProtocolOnce a transaction has passed through the gauntlet of Malice Detection and, if necessary, the Isolation Chamber, it reaches the Transaction Execution stage. This is where verified transactions are finally integrated into the blockchain's reality.
The SLS protocol also integrates malice detection by simulating transactions in different contexts to assess their impact accurately. This hybrid approach combines parallelisation for independent transactions and sequential analysis when context is needed, enabling Zircuit to maintain both security and efficiency.
The SLS Advantage: Proactive Defense in a Reactive WorldWhat makes Zircuit's SLS truly different is its proactive stance. While other systems might detect and react to threats, SLS aims to prevent them entirely. It's the difference between having a security system that alerts you to a break-in and having one that stops the burglar before they even touch your door.
This approach provides four key benefits:
- Enhanced Security: By catching potential threats at the sequencer level, Zircuit creates an additional, powerful layer of defence against attacks.
- Improved Efficiency: Malicious transactions are stopped before they can waste system resources or cause disruptions.
- User Protection: SLS helps protect users from inadvertently interacting with malicious smart contracts or falling victim to sophisticated scams.
- Ecosystem Integrity: By maintaining a clean, secure environment, Zircuit fosters trust and stability in the entire blockchain ecosystem.
With these core principles established, it's important to address some practical considerations—like the impact of added security on transaction speed.
Balancing Security and Latency
When reading about Zircuit, I wondered whether adding an extra verification step would lead to increased latency. Imagine this process like a security checkpoint at an airport. Just as airport security checks every passenger quickly yet thoroughly to ensure safety, Zircuit performs an additional verification step to secure each transaction. The goal is to prevent any harmful elements from passing through while keeping the process efficient and minimising delays. While it might seem like an additional step that could slow things down, it is designed to be quick and efficient.
Although the security element in Zircuit does introduce some latency, it operates at a per-transaction level and remains virtually unnoticeable to users. Once a transaction is accepted into the mempool, the user waits for it to be included in a block, similar to how it works on Ethereum.
Zircuit produces a new block every 2 seconds in contrast to Ethereum’s 12 seconds, and the system is designed so that each transaction analysis fits within that timeframe. Most transactions are analysed in around 100 milliseconds, which means the analysis takes less than 10% of the 2-second block time. Depending on when the transaction arrives at the sequencer node, it can either be included in the current block or the next one, resulting in a maximum latency of up to 4 seconds per transaction.
So, Zircuit adds a little time to your transactions. But most transactions, like simple transfers, swaps, or interactions with a lending platform in a non-flash loan transaction, will immediately go through the SLS security almost 100% of the time.
The next critical question is: how does Zircuit determine what constitutes malicious activity? Zircuit relies on databases of previous hacks, which provide valuable insight into past vulnerabilities and attack patterns. This approach, combined with community input, effectively boils down to a form of social consensus, where collective knowledge is used to identify potentially harmful transactions.
Why Zircuit’s Approach Matters
Zircuit’s combination of batching, parallel proof generation, and oracle-based quarantining makes the blockchain more secure and efficient. By processing transactions in groups and using multiple provers, Zircuit can effectively block harmful transactions while keeping legitimate ones flowing smoothly. Each transaction is thoroughly vetted by an oracle, adding another layer of security. It’s like having multiple checkpoints to ensure that only safe, verified transactions make it through.
The Zircuit team has been building in the space for the past several years. Zircuit is built by a veteran team of blockchain engineers, security researchers and cryptographers with PhDs in Computer Science and related fields. Beyond their academic excellence, they have diverse backgrounds from companies such as Google, MathWorks, Opera, ProtonMail and Samsung. They bring a wealth of security expertise from their former experience at Quantstamp, a leading smart contract security auditing firm.
The core Zircuit team has authored and presented 12+ papers and talks on bridge hacks, rollup escape hatches, bridge architecture and formal methods. They have received 3 Ethereum Foundation grants for researching rollup security, rollup compression and scaling cryptography.
An investor we spoke to who preferred to remain anonymous explained his rationale for backing Zircuit. First, in the endless pursuit of more TPS, we often forget that users prefer security over speed. It does not matter how fast your money moves if you are unsure about its security. So, backing a network that focuses primarily on security would be key to growing the number of users that exist in the industry today. It expands the nature of applications that can be built, too. Second, Zircuit's team is a unique blend of expertise in security and experience in scaling consumer apps. It is not just the "theoretical how" that they possess. They also understand what breaks systems as they scale from their experience over the past few years. The code can be open-source. The expertise cannot be easily forked.
The way Zircuit's tech stack is constructed also puts it in a unique position to serve as a gateway to "safe DeFi usage." Many DeFi users and whales have been burned in the past and are now looking for safer yield opportunities. Zircuit’s SLS model shines in this context by adding an extra layer of safety to protocol audits at the sequencer level.
This detailed supply chain approach to handling transactions is what sets Zircuit apart. By treating each transaction like a package that goes through multiple levels of inspection, Zircuit ensures the integrity of the blockchain. This approach protects it from both small-scale fraud and large-scale coordinated attacks.
From a developer's perspective, Zircuit helps them make their applications more secure. Traditionally, developers of DeFi applications have had to undertake a series of complex measures to secure their protocols. These steps include obtaining an audit, setting up alert systems for potential exploits, understanding the nature of any exploit, responding effectively by pausing or freezing contracts, and managing the reputational and financial fallout afterwards.
This process demands significant time, technical expertise, and the ability to respond immediately when threats emerge. In addition, the DeFi application’s developer team has to be globally distributed to cover all time zones.
Consider the recent exploit of Penpie , where attackers drained significant funds due to a vulnerability in the smart contract. The developers had to quickly understand the nature of the exploit, pause the contract, and address the aftermath, including tracing stolen funds and managing reputational damage.
If Zircuit had been in place, it would have done more than just flag the suspicious transaction—it would have fundamentally changed the outcome in three crucial ways. First, by detecting and quarantining the malicious transaction before execution, it would have prevented the hack from occurring.
Second, the quarantine analysis would have provided the development team with detailed information about the targeted vulnerability, offering valuable technical insights.
Third, this early warning system would have given the team time to implement a complete fix for the vulnerability. Or, if a fix wasn't immediately possible, allow users to safely withdraw their funds. This would prevent both financial losses and reputational damage. This proactive approach transforms crisis management into risk prevention, fundamentally changing how protocols handle security threats. This would have provided a crucial window to prevent the exploit from impacting the protocol and saved both the developers and users from significant financial and reputational losses.
Zircuit simplifies this process by taking on much of the security load. Instead of developers being solely responsible for every aspect of security, Zircuit's SLS integrates these protective measures directly at the transaction level. This extra layer of scrutiny acts like a built-in security guard, identifying potentially malicious transactions before they are added to the block.
In a way, Zircuit is like additional coverage for your insurance at zero cost—since the security it provides comes at no additional expense to developers. If you were offered additional coverage on your travel insurance for free, you would take it, right? Similarly, Zircuit offers developers a safety net without any incremental cost.
This means developers can focus more on building their applications rather than worrying about constant monitoring, response mechanisms, or the fallout from potential security incidents. By effectively adding an automatic layer of real-time security at the sequencer level, Zircuit serves as a gateway to safer DeFi usage, allowing users to trust the platform with their transactions and reducing the burden on developers to manage all security aspects alone.
Zircuit Ecosystem
All of this is great. But can Zircuit get to product-market fit? How does the landscape look today? What is Zircuit’s go-to-market (GTM) strategy?
Liquidity on a chain is one of the scarce resources for DeFi protocols. Apart from incentives, liquidity is probably the single most important parameter for DeFi protocols. A chain with higher liquidity will almost always attract more traders and investors, and thus, DeFi protocols. Zircuit’s GTM was availing of the points meta by distributing points to users who staked on Zircuit using re-staking protocols like EtherFi, Swell, and Renzo.
A key partnership is with Catizen, Telegram's leading blockchain game with over 3 million users and 400,000 daily active users. By deploying their game on Zircuit, Catizen will help introduce blockchain gaming to their substantial user base in a secure environment. This partnership demonstrates Zircuit's appeal beyond pure DeFi applications. In addition, the Zircuit team is incubating a fair launch consumer AI project, which will be publicly announced very soon.
Zircuit has also formed a significant alliance with EigenLayer, executing a well-received fairdrop that allocated 2% of ZRC supply to over 200,000 EIGEN token holders. This strategic distribution, targeting users holding a minimum of 3 EIGEN tokens, has garnered strong support from the EigenLayer community and team. The endorsement from prominent figures like EigenLayer founder Sreeram Kannan and ETHSingapore founder fishbiscuit underscores the industry's confidence in Zircuit's vision.
Zircuit currently has over $2B worth of total value locked (TVL). Comparing TVL with other L2s on L2Beat , it ranks 4th, just above Scroll ($1.5B) and below Arbitrum (%13.8B), Base ($8B), and OP Mainnet ($6.6B). Please note that this is only the liquidity hub TVL. This is designed to reward participating users and communities that help bootstrap native, day-one liquidity to Zircuit.
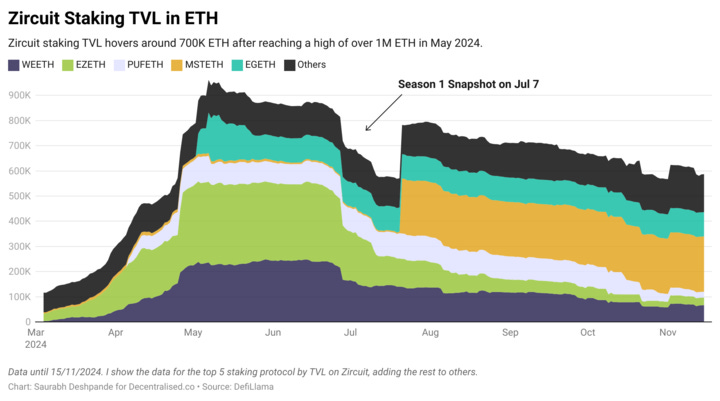
With security at the centre and amassing over $2B in staking TVL, Zircuit remains focussed on DeFi and Infrastructure, with a few applications being developed in the social category.

This is not intended to be an exhaustive map but a representation of applications building on top of Zircuit. Source: Zircuit
Zircuit's Moment of Truth: Can It Win the Long Game?
Zircuit acts as zero-cost additional security for developers. If all else is equal, the Nash equilibrium suggests that developers will build their DeFi apps on Zircuit. But, it's not always that simple.
An established L2 like Arbitrum or Base could potentially offer something similar to Zircuit. But replicating Zircuit's approach is not straightforward because security isn't embedded in their DNA. Just as many have copied Uniswap’s model, Uniswap remains the leader due to its foundational strengths. Similarly, the Zircuit team has over seven years of experience in smart contract auditing—expertise that very few teams in the crypto space possess. This deep background creates a high barrier to entry for competitors.
Unlike projects that merely promise future security features, Zircuit's SLS is already live and operational, actively protecting transactions on their network. This combination of proven expertise and working technology sets Zircuit apart in an industry where security solutions often remain theoretical. In addition, they are highly dependent on cumbersome processes like formal verification. It demands a lot of human capital.
Hackers are always trying to stay one step ahead, but Zircuit fundamentally changes this dynamic. Not only does Zircuit's system detect and block known attack patterns, but its AI-powered security layer can also identify new, suspicious behavioural patterns that deviate from legitimate transaction norms. This means hackers face a dual challenge: they must not only devise entirely new attack methods, but these methods must be so innovative and sophisticated that they can evade an AI system trained to recognise malicious patterns—even ones it hasn't seen before. This raises the bar significantly, making successful attacks exponentially more difficult and costly to execute.
Crypto is largely driven by incentives, which can attract users, liquidity, and developers in the short term. We've often seen that the market can remain irrational for longer than you can remain solvent. For example, consider the Bitcoin L2 landscape. Several L2s have emerged that are not well differentiated and are struggling to gain adoption. It takes time to get sticky adoption. So, it is possible that other L2s or chains take user and developer attention away from Zircuit.
But, long-term success is driven by valuable and differentiated offerings. There is already some evidence that the market is taking notice. During the sideways market in 2024, Zircuit maintained a TVL of ~$1.5B to $2B. It shows the faith users put in Zircuit.
Zircuit’s value proposition is also attractive for players such as financial institutions and RWA protocols, as they rely on minimising risk and avoiding transactions with compromised or malicious counterparties due to operating within regulatory boundaries and compliance requirements. As the ecosystem continues growing, it will be interesting to see more of these use cases emerge on Zircuit.
Zircuit's unique approach to security provides lasting value by offering a zero-cost solution that continually forces bad actors to adapt, making exploits increasingly challenging. While short-term incentives may attract users temporarily, it's the robust, differentiated security model that will win in the long run. To build trust, Zircuit must prove its effectiveness by preventing a few significant hacks. Once it demonstrates this capability, developers will see the clear benefit of getting an additional line of defence at no cost, helping create a safer ecosystem for everyone.
Thinking about sentient beings, Saurabh Deshpande
Disclaimer - DCo members may have positions in assets mentioned in the article. No part of the article is financial or legal advice.
Disclaimer: The content of this article solely reflects the author's opinion and does not represent the platform in any capacity. This article is not intended to serve as a reference for making investment decisions.
You may also like
2024 Crypto Developer Report SummaryExecutive Summary

Digital Veblen Goods and Fees

Musings on the Future of Actually Smart Wallets

Bitwise CIO: Биткойн может достичь $200 000 без краха доллара